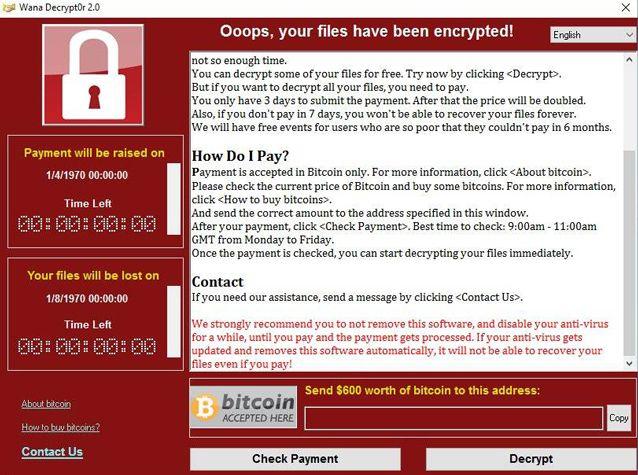
RANSOM: The WannaCry lockdown screen. If you see this it is already too late. The hijackers of data are demanding $300 to $1000 for a code which will allow you to access and regain control over your own data
A group of cyber terrorists have used a stolen American security program to hack into computers across more than 150 countries. They have hacked hospitals, automobile plants and other business establishments. This is extortion on a global scale, with the hijackers demanding a fee to free the data that they have blocked
By GO Staff
COMPUTERS in more than 150 countries have been hit by what experts are calling an unprecedented mass cyber attack using ransomware. A report from cyber security company F-Secure suggests that Russia and China were the biggest victims of the attack. F-Secure chalks these countries’ vulnerability up to the fact that many computers in these countries run pirated versions of Windows, which aren’t upgraded frequently.
This is a problem because India is third only to Russia and China in the percentage of computers running pirated software. 70 per cent of Chinese computers use unlicensed software, the Russian figure stands at 64 per cent and India’s at 58 per cent.
The so-called WannaCry ransomware locks access to user files and demands money – in the form of the virtual currency Bitcoin – in order to decrypt them.
Globally experts were scrambling to determine who was behind the May 12 attack, which exploited a security flaw in older versions of Microsoft’s Windows operating software. This includes Windows 7, Windows Server 2008 and Windows XP. Windows 10 is unaffected by the exploit. While Microsoft did issue patches for the exploit in March this year, the scale of WannaCry’s impact is proof enough that PCs weren’t updated in time. Microsoft has taken the unusual step of reissuing security patches first made available in March.
Researchers at the Moscow-based computer security firm Kaspersky Lab said it was seeking to develop a decryption tool “as soon as possible”. Europol provides free decryption downloads for most ransomware already detected, though not yet for this particular attack.
RANSOM DEMANDS
VICTIMS were asked for payment of US $300 (about `19,000) in the virtual currency Bitcoin. Payment is demanded within three days or the price is doubled, and if none is received within seven days, the files will be deleted, according to the screen message. Given the attack’s widespread nature, even such a small sum would stack up quickly, though few victims seem to be paying up so far.
Experts advise people not to pay, as it would only encourage the attackers, there is no guarantee that they will unblock files, and may result in them gaining access to victims’ bank details.
MASSIVE ATTACK
EUROPOL chief Rob Wainwright said more than 2,00,000 victims had been hit in more than 150 countries making it the largest ransomware attack observed in history.
High-profile victims include hospitals in Britain, the Spanish telecoms giant Telefonica, French carmaker Renault, US package delivery company FedEx, Russia’s interior ministry and the German rail operator Deutsche Bahn.
Experts said the ransomware programme appears to support dozens of languages, showing that the hackers wanted to corrupt networks worldwide.
The virus spread quickly because the culprits used a digital code believed to have been developed by the US National Security Agency – and subsequently leaked as part of a document dump, Kaspersky Lab said.
The attack is unique, according to Wainwright, because it combines ransomware with a worm function, meaning once one machine is infected, the entire internal network is scanned and other vulnerable machines are infected.
INDIA IMPACT
QUICK Heal has “detected over 48,000 MS-17- 010 Shadow Broker exploit hits responsible for ‘WannaCry ransomware’ outbreak in India”, the cybersecurity firm said in a statement.
The Pune-based company said 60 per cent of the ransomware attack attempts by the malicious WannaCry virus were targeted at enterprises, while the rest were on individual customers. Quick Heal said there have been over 700 distress calls by customers in the last few days.
Analysts feared that India’s banking system would be struck hard by the WannaCry ransomware, but that doesn’t seem to be the case. One reason for that is the possible slower speeds at which systems operate, including most ATM kiosks, which proved to be helpful in preventing the spread of the malware, which is usually a big file.
Among cities in which sporadic attacks were reported are Ahmedabad, Vadodara, Chennai and Kolkata.
Dhananjay Dwivedi, secretary in the Gujarat government, said there were 120 incidents across the state. “However, there is no harm on government functioning,” he added.
In Kerala, computers in panchayat offices in Wayanad and Pathanamthitta districts were affected. “The staff found MS Word and MS Office files inaccessible,” said Thariyode panchayat president Reena Sunil.
Meanwhile, the Oragadam, TN, factory of alliance partners Renault & Nissan restarted production on Monday after a disruption on Saturday. The attack had affected production of 1,200 vehicles.
In Gorakhpur, UP, a motorcycle dealer was asked to pay $300 to access files on his computer in a pop-up on Saturday.
Computers in at least three locations in West Bengal, including those of a power discom, also came under attack. “The disruption caused was local. It did not affect power distribution, customer data or commercial operations,” said West Bengal State Electricity Distribution Co Ltd Managing Director Rajesh Pandey.
But absence of major hit does not mean that all the systems are safe from future attacks. Caution is key.
PREVENTIVE MEASURES
THE best defense against ransomware attacks is to have all files backed up in a completely separate system. This means that if you suffer an attack you won’t lose any information to the hackers.
Apart from that, if you hope to avoid being infected with the malware, Sunrise technology expert Valens Quinn said the first thing you need to do is “update your Windows software because that’s where the vulnerability is”.
“Update as soon as you log in to your work computer or your home computer this morning,” he said, warning it might already be too late for many. In order to update, you need to log on to the internet which will leave you vulnerable. If you log on to find the red lockout screen on your computer, Quinn said paying up is no guarantee you will be free of the ransom ware.
“If you do pay they may or may not unlock your computer. They may ask you for more money after the first payment,” he said. “They may unlock it but not really remove the software after the first payment and lock it again later. But really, there is nothing you can do at the moment to get the stuff off your computer once the ransomware is installed.”
As with all things technological, Quinn said “prevention is the best measure” to prevent leaving yourself open to extortion. Do regular backups of you computer. Another is always update your software, have internet security software installed and updated as much as possible. Maybe having a firewall installed will prevent your computer from being hacked as well.”